Cyberattacks are becoming more complex as insider threats rise. Traditionally, enterprises used perimeter protection and trusted anyone and anything within the perimeter with their sensitive information. This old method was prone to insider attacks, especially for organizations that depend heavily on on-site infrastructure.
For an extra layer of protection, businesses are increasingly adopting the zero-trust security model. The new system focuses on comprehensive authentication and monitoring. This guide explains why the zero-trust method is essential for on-premise environments, and a step-by-step implementation plan.
What is Zero Trust Architecture
Zero Trust Architecture is a security framework that works on the principle of “never trust, always verify.” Traditional models unquestioningly trust users and devices inside the network perimeter. In contrast, the new system assumes that threats can originate from anywhere, both within and outside the network. That means anyone or anything accessing the network must be verified based on their access rights.
Forrester Research introduced the idea in 2010 as a focused approach to security threats. The idea uses technologies like multi-factor authentication and endpoint security. It also became popular in 2020 after the NIST Special Publication formalized it and provided guidance for government agencies and businesses.
Why ZTA is Essential for On-premise Environments
The model is often associated with cloud-native systems. However, many modern organizations operate in hybrid environments or maintain legacy systems that cannot be migrated. These on-site systems usually have outdated security measures, limited visibility, or poor segmentation. Using ZTA in on-premise environments provides extra protection by:
- Preventing insider threats
- Minimizing lateral movement in case of data theft
- Improving compliance with regulatory bodies like GDPR and HIPAA
Key Principles of Zero Trust Architecture
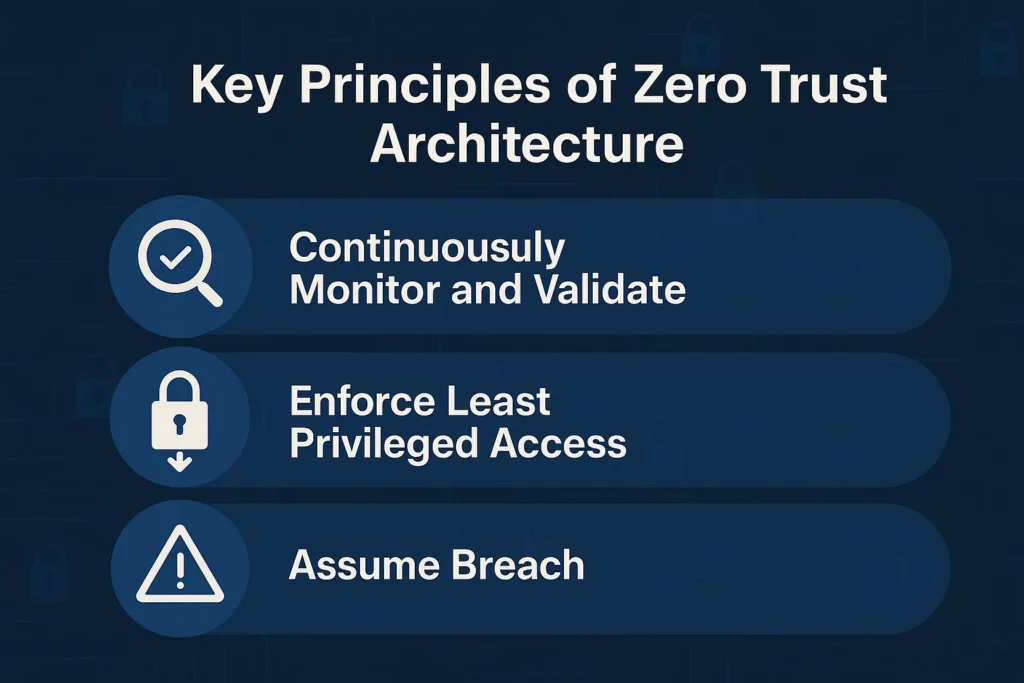
ZTA is based on three key principles that work in conjunction to enforce strict security protocols. That is especially true for modern on-premise environments where traditional perimeters no longer provide adequate protection. This include:
Continuously Monitor and Validate
ZTA demands constant monitoring to detect unusual behavior. Organizations should validate users’ authenticity based on the available data points. These include location, user identity, data classification, and services or workload.
Enforce Least Privileged Access
The principle restricts user’s and applications’ right to only the data and services they need to perform their authorized tasks. This reduces potential damage in case of compromised credentials or insider threats. The rule is enforced by security strategies like granular access controls and just-enough access.
Assume Breach
The new model assumes that attacks can happen at any time from within or outside the network perimeter. This helps businesses implement measures that limit the potential damage. These measures include micro-segmenting sensitive resources, encrypting data flows, and implementing robust incident response and recovery mechanisms.
Steps to Implement the Architecture
ZTA is a proactive approach that encompasses the organization’s employees, users, and the Internet of Things. Setting up the system is a process that requires planning and well execution. Below are key steps to set up ZTA in on-site environments.
1. Define the Protect Surface
Identifying the protect surface is the first step in implementing a zero-trust model. Unlike the vast and ever-changing attack, the protect surface include only the most critical and sensitive assets that need protection. These include customer records, domain controllers, the company’s financial data, and legacy systems that cannot be moved to the cloud.
Organizations can start by creating comprehensive lists of all internal users and third parties that need access to the network. They can use reliable data extraction services, such as OCR Studio, that collect and verify user-sensitive data while complying with GDPR requirements. Recording all devices that connect to the network also reduces insider threats, especially those resulting from Bring Your Own Device(BYOD) policies.
2. Identify Sensitive Data
After defining what needs protection, the next step is to locate and classify sensitive data within the environment. This involves scanning storage systems, databases, and file repositories. Categorizing data based on sensitivity and compliance needs also ensures the right people and devices have access to it. Tagging data also helps in enforcing access controls and encryption policies.
Identifying and categorizing sensitive data ensures that the system prioritizes the most valuable assets. The process also allows organizations to align with regulatory mandates. However, businesses should regularly review classifications to ensure they remain relevant to the evolving ecosystem.
3. Establish Strong Identity and Access Management Policies
Identity and Access Management guidelines govern the entire security framework within an organization. Having the policies ensures that only authorized users can access sensitive resources. Steps to set up these guidelines include implementing multi-factor authentication, Single Sign-On, and device posture assessment.
The step is essential to ensure the ZTA aligns with the established security principles. Enterprises can use the Kipling Method, which examines each network interaction to ensure every access is fully verified. This helps them integrate the policies with their existing infrastructure.
4. Design Zero Trust Architecture
With clear policies and data categories, firms can move on to design a Zero Trust Architecture. The model serves as the network’s structural security framework, comprising several key components. These include micro-segmentation, where the network is divided into smaller segments with individual access policies. Businesses can use software-defined networking to implement this.
Deploying firewalls or secure gateways at strategic points allows organizations to control access between segments. The step can include the use of Security Information and Event Management (SIEM) solutions to gather and analyze logs. This ensures the system supports visibility and flexibility, allowing it to adapt to future threats.
5. Implement Zero Trust Network Access
Zero Trust Network Access (ZTNA) replaces the traditional VPNs with a more secure, application-aware access model. It ensures that users only access the specific applications and resources they are authorized. It also includes key components such as contextual access policies, application-level tunneling, and continuous verification.
ZTNA evaluates critical factors like the device’s security posture and the location from which the request is made. It is essential to thoroughly scrutinize all access requests based on the available security protocols. This is especially true for on-site infrastructure that needs robust support.
6. Automate Continuous Monitoring
Setting up automatic monitoring is essential for detecting threats in real time and enforcing the policies. The step involves regular audits and adjustments to security features to ensure they remain ahead of evolving attacks. Organizations can use SIEM solutions and automated incident response tools. This reduces human error and enhances response speed and consistency.
Endnote
ZTA is an important security tool for legacy environments where demand for on-site infrastructure still matters. Its implementation can be challenging. However, the benefits of reduced risk and improved visibility make it a worthwhile investment. By following the step-up steps above, organizations can protect their sensitive information against today’s changing threats.